Spring Saml After Authentication Still Its Going for Sso Login Updated FREE
Spring Saml After Authentication Still Its Going for Sso Login
Recently I've been working on integrating SSO in an former Spring projection and for that very reason, I created a small PoCto get my hands on Leap SAMLand all its subtleties. In this article, I am going to share my feel of adding Spring SAMLto a Spring MVC projection and integrating information technology with SSOCircle. Bound did a wonderful job of documenting everything SAML related, setting upward the .xml configuration, and fifty-fifty SSOCircle integration, merely in that location are places where you could still fall. So before reading this article make certain to read the whole Spring SAML documentation and SAML documentation itself.
I would assume that y'all already are familiar with the concept of SSO and its details, just for the sake of a better understanding of the article and the keywords that I'm going to use I will briefly describe the basics of SSO.
What Is SSO?
Unmarried sign-on (SSO) is an hallmark scheme that allows a user to log in with a single ID and password to whatsoever of several related, even so independent, software systems - Wikipedia
So there are several related, yet contained, software systems – service providers and an entity that checks the user'southward identity – identity provider. And then there is a secure way for these 2 to communicate and 1 of the most-used security languages that define the relationship between identity providers and service providers is Security Assertion Markup Linguistic communication (SAML).
The Security Assertion Markup Language (SAML), adult by the Security Services Technical Committee of Haven, is an XML-based framework for communicating user hallmark, entitlement, and attribute information. As its name suggests, SAML allows business organization entities to brand assertions regarding the identity, attributes, and entitlements of a discipline (an entity that is ofttimes a human user) to other entities, such as a partner company or some other enterprise application. - OASIS
At that place are:
- Service Provider (SP) – the awarding providing services
- Identity Provider (IdP) – the entity providing identities
- SAML – the language of advice between SPand IdP
- SAML Request – hallmark request (
AuthNRequest) - SAML Response – assertion of the authenticated user (
AuthNResponse) - Assertion- a package of information that supplies zero or more statements made by a SAML authority
- SAML Request – hallmark request (
Permit'south run into a brief overview of how everything assembles

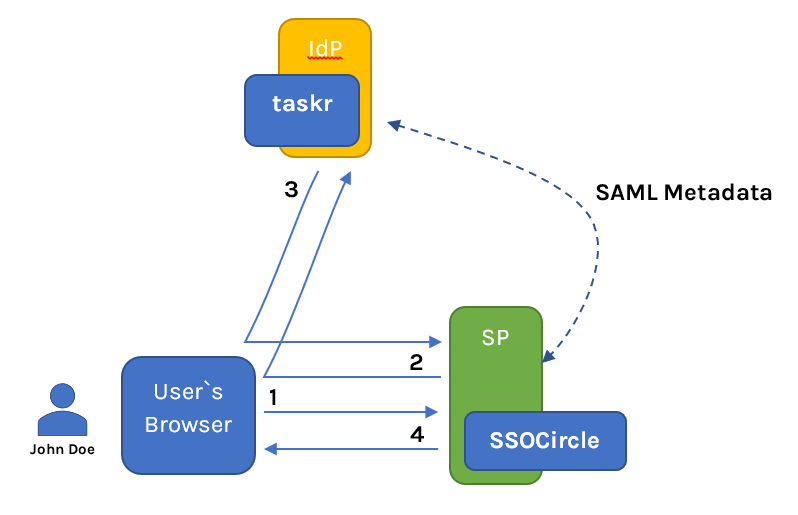
Having a user named John Doe:
- John Doe via the browser tries to admission the SP
- SPredirects to the IdPfor the identity bank check/hallmark
- IdPreturns the SAML response to the SP via the browser's redirection
- Based on the response SPsends the requested resource or handles the error
At present for this advice to work IdP and SP need to know about each other, and this is washed via the SAML metadata. SAML Metadata is an XML document containing various of import information about IdP/SP. Typically the SP will generate one metadata containing URLs, IDs, a public cardinal, and other SAML-related information for IdP to import it and the same goes for the IdP – SP will import IdP's metadata.
At present that we have some understanding of what is going on, allow's have a quick look at the application. The application is a simple task manager (things to practise manager) named taskron Spring Boot with Thymeleaf. taskrenables its user to create/delete and view tasks, yous tin bank check it on GitHub. And so there is SSOCircle which is the IdP for taskr.
Let's have a await at the SAML configuration of the taskr
Cryptography
Basically what you lot run into is what the Spring documentation already offers with some small adjustments. At present I want to talk nigh some things that in my opinion are tricky.
Outset of all, is the keyManager
SAML advice uses cryptography for signing and encryption of the data and everything this related is washed through the keyManagerwhich relies on a single JKS key store containing all the private and public keys. To generate a key shop I've used the following command:
keytool -genkeypair -alias taskrSaml -storepass 123456
-dname "CN=John Doe, OU=Taskr, O=EvilInc, 50=Cupertino, S=California, C=US"
-keypass 123456 -keyalg RSA -keysize 2048 -sigalg SHA256withRSA
-keystore taskrSamlKeystore.jks
And and then you tin identify it under your resources and provide the path. Also, note that at that place is KeyStore Explorer which facilitates easy handling of the key stores and information technology comes in very handy when you have to bargain with importing the IdP certificates. Some other thing to mention here is that Mavenmight corrupt your .jks file during the build process and it becomes unusable, so to deal with that I added the following plugin in pom.xml under the build plugins.
Since I've already mentioned the IdP signing/encryption certificates let's discuss them. IdP certificates may be provided by the person treatment the IdP or y'all can grab them from the IdP'due south metadata. SSOCircle'southward metadata URL is https://idp.ssocircle.com/idp-meta.xml (please note this is the same URL used for the HTTPMetadataProvider bean initialization) and opening that yous want to search for the following 2 tags
-
<KeyDescriptor use="signing"> -
<KeyDescriptor utilize="encryption">
These are client certificates provided by SSOCircle as a hateful of strong hallmark, simply the integration works without adding them into your central store as well. Some IdPs might require a signature trust institution, so for that reason, I'm going to explain this. Under them, in the <ds:X509Certificate> tag you'll find IdP's certificates. I created 2 files with the .p12 extension, i for the signing certificate, and the other for the encryption document and I pasted the content of the X509Certificates between these 2 lines.
-----Begin Document-----
-----END CERTIFICATE-----
After that, I imported them into my key store using KeyStore Explorer – Import Certificate.
Existence on the cryptography topic, permit'due south discuss some other interesting thing - samlBootstrap bean. Though integrating with SSOCircle almost probably yous won't encounter this problem, but dealing with other IdPs you might go an fault proverb that the message is not signed with the expected signature algorithm, and that bulletin is signed with the signature algorithm SHA1whilst the expected one is SHA256. That is considering SAML by default signs its letters with SHA1and to overcome that, we demand to explicitly specify the signature algorithm and digest method via a custom SAML bootstrap.
Communication
Allow's talk about communication, how IdP is going to know where to redirect, or where to address its requests. It is already mentioned in the Spring SAML documentation.
In case y'all use automatically generated metadata make certain to configure entityBaseURL matching the front-end URL in your metadataGeneratorFilter bean - Leap Docs
so setting this URL in metadataGenerator edible bean in the metadata you'll go generated the following URLs :
http://localhost:8080/saml/SingleLogout
http://localhost:8080/saml/SSO
This unremarkably is enough to establish the advice between the SP and IdP, merely if you're facing a situation where multiple dorsum-end servers process SAML requests forwarded past a opposite-proxy/load balancer or you're trying to expose your local URL using due north grok, then you might need to configure another SAMLContextProvider.
As information technology is already well-documented I desire to mention just one affair, brand sure to set samlContextProviderLB.setIncludeServerPortInRequestURL(true); if you're dealing with your server port and y'all need information technology in your URL. Too pay attention that if the server port is less or equal to 0 the port won't be included in the URL, might come in handy when you are dealing with multiple environments with different URLs.
Since we are talking about URLs, I want to tell y'all some other interesting thing that I encountered, I telephone call it "Cyclic SAML Authentication", but kickoff a little preface. When you are dealing with SAML you tin can configure 2 kinds of logouts: local logout and global logout.
- Local logout logs you lot out just out of the current SP'due south session, but keeps your IdP session and allows the user to apply other SPs however being authenticated. Local logout can be invoked at
saml/logoutby specifying thelocalrequest parameter equal totrue(http://localhost:8080/saml/logout?local=true). - Global logoutlogs yous out of IdP terminating all the SPs sessions forcing the user to enter his credentials once again at the IdP to access any of the SP and tin be invoked at
saml/logoutwithout specifying any parameters.
Some other thing to mention related to the user's session is that you might get a bulletin stating that the authentication argument is too erstwhile to exist used if you don't get in sync the maximum authentication age of your SP and IdP. You can fix this problem past setting the property on the webSSOprofileConsumer bean. You might be tempted to utilize the Integer.MAX_VALUE equally a maximum authentication age, but this will result in not checking the authentication statement at all or it won't even work every bit information technology happened to me.
Now, what happens after you log out? What I have experienced is that either you log out locally or globally you get redirected to "/" and therefore not being authenticated you automatically get redirected to the login page at IdP in instance of a global logout or you lot're getting a new session which redirects you to the requested page in case of a local logout.
So from a UX perspective, the local logout doesn't make any sense you try to logout from the current SP and so you become to employ it again after some redirection equally if you lot never logged out. A solution would exist to create an unsecured login or logout page on the SP side and whenever the user locally logs out yous redirect him in that location and let him determine if he wants to login again or non (saml/login). So to configure that you demand to specify the logout success URL
And for information technology to work I registered the hallmark entry point like this
IdP Configuration — SSOCircle
And last but not least I wanted to share my feel on SSOCircleconfiguration. Starting time what you want to practice is to create an account on SSOCircle. The user that yous'll be creating here will exist the user of your SP.
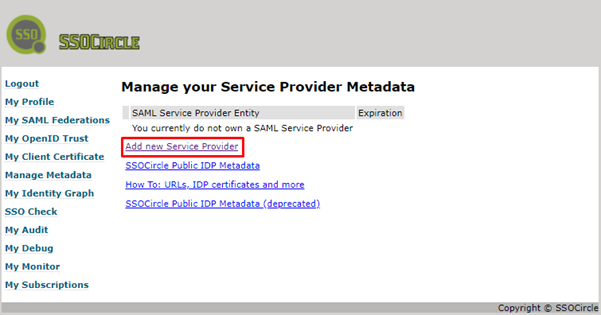
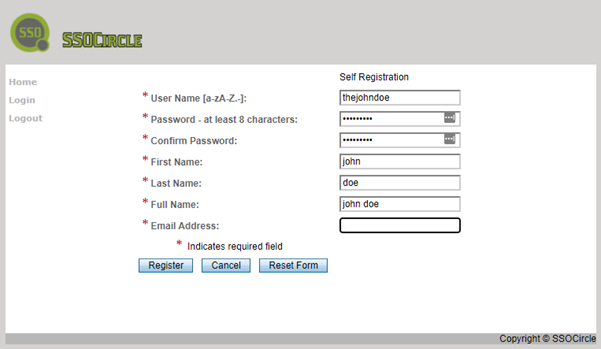 Once you accept your user you need to add the service provider to SSOCircle.
Once you accept your user you need to add the service provider to SSOCircle.
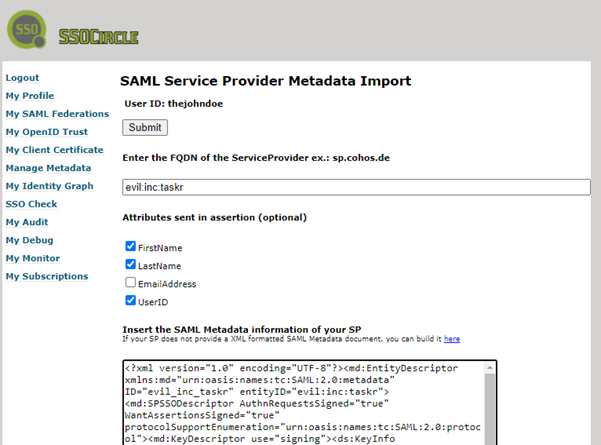
On the side by side page, y'all need to enter the SP'south id, metadata, and cheque the needed assertions that you're going to validate via your custom SAMLUserDetailsService.
The SP's id is the same id used in the metadataGenerator as the entityId and the SP's metadata can be grabbed at http://localhost:8080/saml/metadata
That's it, I hope, you've learned something.
Topics:
java, sso, sso authentication, saml, thymeleaf, spring boot, java configuration, spring, tutorial
Opinions expressed past DZone contributors are their own.
Spring Saml After Authentication Still Its Going for Sso Login
DOWNLOAD HERE
Source: https://dzone.com/articles/diving-into-sso-with-spring-saml-and-ssocircle-pit
Posted by: weymouthbutioned.blogspot.com
Comments
Post a Comment